

Monthly Threat Report December 2023: Holidays Bring Malicious Email and Lots of Patches to Apply
Introduction
The Monthly Threat Report by Hornetsecurity brings you monthly insights into M365 security trends, email-based threats, and commentary on current events in the cybersecurity space. This edition of the Monthly Threat Report focuses on data from the month of November.
Executive Summary
- While those email threats categorized as “Threats” and “AdvThreats” are down, the amount of low-effort, easily-detected email threats is up. That said, the overall email threat landscape remains dangerous with a high volume of malicious traffic, which is common for this time of year.
- The usage of HTML and PDF files to deliver malicious payloads in email attacks is up for this reporting period.
- Every industry, except for the transport industry, has seen an increase in email-based threats over this data period.
- DHL remains the most impersonated global brand in email attacks.
- We’ve seen a noted increase in M365 brand impersonations, likely driven by the increased popularity of reverse-proxy phishing kits like EvilProxy.
- Hacktivists breached the US Department of Defense-run Idaho National Laboratory and many employee records were leaked on the dark web. This continues to add weight to international conversations about regulating cybersecurity practices.
- Microsoft fixed 63 security vulnerabilities during its monthly patch on Tuesday. This includes five zero-day vulnerabilities. Organizations are urged to apply fixes as soon as possible.
- Major vulnerabilities in Intel and AMD CPUs put multi-tenant deployments at risk. Patches are available.
Threat Overview
Unwanted Emails By Category
The following table shows the distribution of unwanted emails per category for October 2023 compared to November 2023.
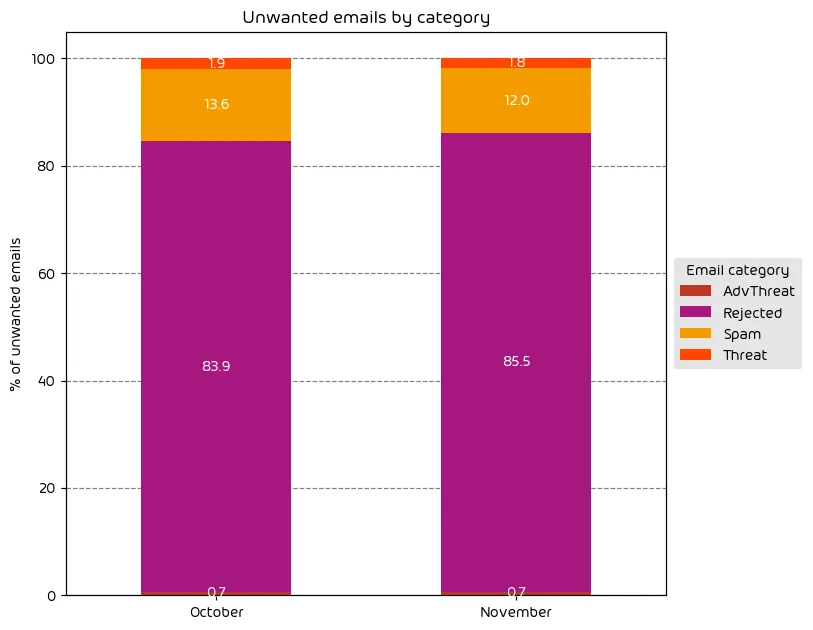
This month’s report shows that the email threat landscape is quite similar to the previous data period. The number of email threats remains high, but we’re seeing a slight increase in “low-effort” email attacks that quickly get categorized as “Rejected.” This is likely because we’re currently in the middle of the holiday season, and threat actors are looking to sustain high amounts of simple attacks to catch people unaware. This is a common trend we see every year around this time.
NOTE: As a reminder, the “Rejected” category refers to mail that Hornetsecurity services rejected during the SMTP dialog because of external characteristics, such as the sender’s identity or IP address. If a sender is already identified as compromised, the system does not proceed with further analysis. The SMTP server denies the email transfer right at the initial point of connection based on the negative reputation of the IP and the sender’s identity.
Other categories in the image are described in the table below:
| Category | Description |
| Spam | These emails are unwanted and are often promotional or fraudulent. The emails are sent simultaneously to a large number of recipients. |
| Threat | These emails contain harmful content, such as malicious attachments or links, or they are sent to commit crimes like phishing. |
| AdvThreat | Advanced Threat Protection has detected a threat in these emails. The emails are used for illegal purposes and involve sophisticated technical means that can only be fended off using advanced dynamic procedures. |
| Rejected | Our email server rejects these emails directly during the SMTP dialog because of external characteristics, such as the sender’s identity, and the emails are not analyzed further. |
File Types Used in Email Attacks
The following table shows the distribution of file types used in email attacks throughout the data period.
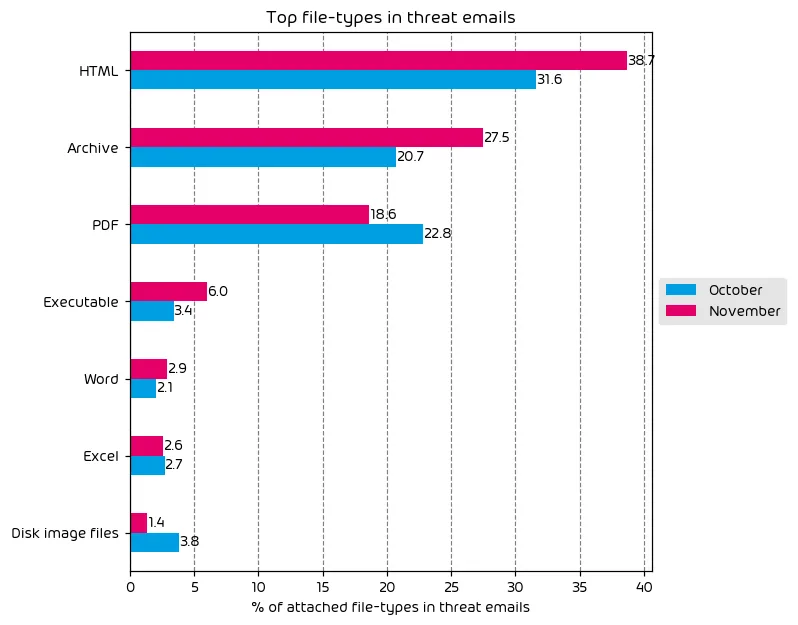
Despite the subtle change in the categorization of email traffic over this data period, the file types in email attacks have notably changed compared to the previous month. The usage of HTML and Archive files has risen, with HTML files accounting for nearly 40% of all malicious file types during the reporting period.
HTML and archive files are both file types usable on several different platforms. Regardless of the target’s operating system or platform, the victim can most likely interact with the malicious payload somehow, making these file types popular amongst threat actors.
Industry Email Threat Index
The following table shows our Industry Email Threat Index calculated based on the number of threat emails compared to each industry’s clean emails (in median). Different organizations receive a different absolute number of emails. Thus, we calculate the percent share of threat emails from each organization’s threat and clean emails to compare organizations. We then calculate the median of these percent values for all organizations within the same industry to form the industry’s final threat score.
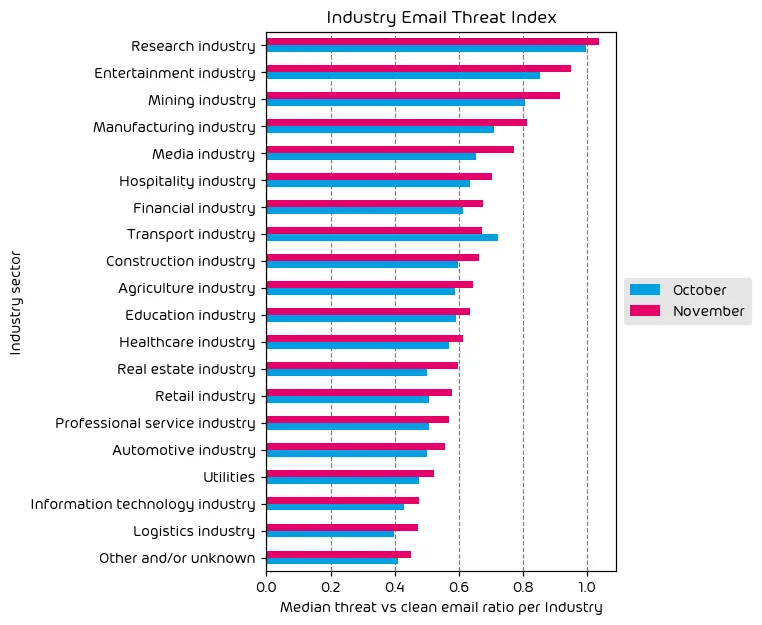
Except for the transport industry, our data shows more threats were levied against EVERY industry vertical during November than the previous month. Again, this trend indicates the holiday season in which we see the number of email-based threats increase.
That said, we have observed that the amount of threats has increased for some industries more than others. For example, Mining, Manufacturing, and media organizations saw the most significant increases. Manufacturing and mining can both be seen as focused targets because it is the end of the year, and many organizations are attempting to make quotas, driving the need for orders and raw materials. On the other hand, the media industry is often a prominent target of nation-state actors looking to influence global discussion and standing through misinformation.
Regardless of your industry, however, our data shows that it DOES NOT matter what industry vertical you’re in. If you can pay a ransom, your organization is a potential target.
Impersonated Company Brands and Organizations
The following table shows which company brands and organizations our systems detected most in impersonation attacks.
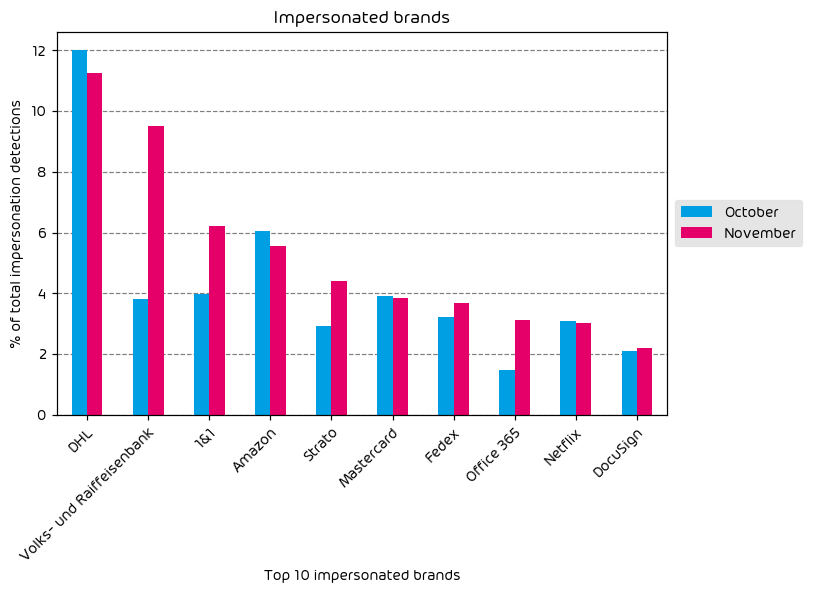
The data regarding impersonated brands in email attacks has also shown some stark differences this month. We’ve observed a significant increase in malicious emails targeting German banking and German telecom company 1&1. More interestingly, though, we’ve seen a noted uptick in M365 brand impersonations.
Reverse Proxy phishing kits, like EvilProxy, have become a popular tool amongst threat-actor groups as of late. These types of tools make it simple for threat actors to gain access to M365 session tokens. The victim believes they are signing into a legit M365 portal, and once they’ve entered their credentials, they’re directed to the real M365 portal, thinking nothing is amiss. The real nefarious thing about this attack style is that once the threat actor has a valid session token from Microsoft Entra from the victim, they can log in as that user while bypassing MFA protections.
This increase can be attributed to the rise in popularity of such tools.
Major Incidents and Industry Events
Hacktivists Breach INL (Idaho National Laboratory)
Upon first glance, some may think SiegedSec’s breach of INL was just another everyday cyber attack. That’s until you realize that INL is a nuclear research center under the purview of the US Department of Energy. Even though no research material is thought to have been pulled from INL’s network by the attackers (as yet report), staff and HR-related records were, in fact, exfiltrated and leaked online.
The breach of a government-sponsored entity isn’t a new occurrence. However, looking at this incident through the scope of other government-related breaches brings weight to the argument for government oversight in cybersecurity practices. We’ve discussed in this monthly report that the governments of the world are increasingly beginning to lose patience, and some early signs of government intervention and regulation are starting to look possible. This was most recently clear in the aftermath of the Storm-0558 breach that led to information being stolen from the US State Department. Other governments across the world from the EU to Australia have also started invoking additional cybersecurity regulations as well. Time will tell what impacts said regulation will have on the industry.
A Doozy of a Patch Tuesday
Many patch-Tuesdays from Microsoft come and go without much fanfare, but the November patch-Tuesday was significant. The November collection of patches from Microsoft addressed 63 vulnerabilities INCLUDING 5 Zero-Days with a CVSS score of 6.5 or higher.
A summarized list is shown below:
- CVE-2023-36025 (CVSS 8.8): SmartScreen security bypass vulnerability, allowing attackers to bypass Windows Defender SmartScreen checks.
- CVE-2023-36033 (CVSS 7.8): Windows DWM Core Library privilege escalation vulnerability allowing attackers to achieve SYSTEM level privileges.
- CVE-2023-36036 (CVSS 7.8): A Cloud Files Mini Filter Driver elevation of privilege vulnerability. This CVE can also escalate the attacker to SYSTEM-level access.
- CVE-2023-36038 (CVSS 8.2): ASP.NET Denial of Service Vulnerability.
- CVE-2023-36413 (CVSS 6.5): A Microsoft Office Security Feature Bypass. It could potentially allow unauthorized access to Office applications.
Reptar and CacheWarp: New CPU Vulnerabilities in the Wild
There are a pair of new CPU vulnerabilities from this past month that are going to require the attention of security teams. Both Intel and AMD have issues that need to be addressed and have provided patches for the vulnerabilities. What’s so interesting about these particular flaws is that they both can impact dense multi-tenant deployments, like large cloud hosting services. That said, while the large cloud hosting platforms are applying patches, so should you if you’re running on-premises data centers.
More details below:
AMD CacheWarp
CacheWarp is an exploit that allows a threat actor to infiltrate virtual machines protected by AMD’s Secured Encrypted Virtualization technology and is being tracked under CVE-2023-20592. AMD has released a patch HERE.
Intel Reptar
Reptar is an exploit that not only allows an attacker to bypass CPU security boundaries but potentially causes denial of service along with privilege escalation as well. This vulnerability is being tracked as CVE-2023-23583 and a fix is available HERE.
Predictions for the Coming Months
- Holiday-driven spam and malware campaigns will continue throughout the next month or two, with shipping and financial brands continuing to be impersonated in such attacks.
- More information is likely to come out regarding the INL breach. It is expected to spur additional discussion within the US federal government regarding cybersecurity best practices within government agencies and related.
- Recently disclosed Zero-Days are likely to see exploitation in the wild. Yes, patches are available, but they take time to apply, and the race is on between threat actors and defenders.
Expert Commentary from Hornetsecurity
We asked some of our internal experts about the news from this month. We have posted their responses below!
From Umut Alemdar, Head of Security Lab, on the importance of proactive cybersecurity measures during the holiday season:
The holiday season often marks an escalation in cyber threats, a trend that becomes more challenging due to the reduced availability of security teams who might be on vacation. A prime example was the zero-day vulnerability CVE-2021-44228 (log4j), which emerged shortly before Christmas and caught many organizations and IT teams off guard. This incident highlights the need for organizations to remain on high alert during the holidays and promptly apply security patches, especially for critical vulnerabilities like zero-day exploits. It also helps to raise awareness against seasonal phishing attacks.
From Andy Syrewicze, Security Evangelist, on CPU Microcode Updates:
I come from a background of infrastructure management, so infrastructure security is always top of mind for me. When I see vulnerabilities like CacheWarp and Reptar show up in the industry I often think back to organizations I’ve advised in the past that haven’t put much emphasis on NON-OS patches (like a microcode update). I would urge admins to NOT delay on rolling out the fixes for CacheWarp and Reptar. These vulnerabilities are just as real and dangerous as an OS-level vulnerability. This is especially true, in this case, for multi-tenant environments. If you work with a hosting provider for IaaS services, make sure you check with them and ask about their plans for deploying the applicable fixes from AMD/Intel. Today’s threat-actors will use any and every vulnerability at their disposal to launch attacks, and CacheWarp and Reptar are no exception.
Monthly Recommendations
- Continue to communicate with end-users regarding the holiday uptick in malicious email traffic and adopt a next-generation email security solution if you don’t have one in your environment today.
- If your organization has not yet applied Microsoft’s security fixes from November, it is HIGHLY recommended that you do so.
- Urgently take steps to apply the CPU microcode updates from Intel and AMD – especially if you are a hosting organization.
About Hornetsecurity
Hornetsecurity is a leading global provider of next-generation cloud-based security, compliance, backup, and security awareness solutions that help companies and organisations of all sizes around the world. Its flagship product, 365 Total Protection, is the most comprehensive cloud security solution for Microsoft 365 on the market. Driven by innovation and cybersecurity excellence, Hornetsecurity is building a safer digital future and sustainable security cultures with its award-winning portfolio. Hornetsecurity operates in more than 120 countries through its international distribution network of 12,000+ channel partners and MSPs. Its premium services are used by more than 125,000 customers.


